Project Delivery Plan
This (generic) project delivery plan proposal is based on our extensive experience with implementing Identum’s IAM-solution (Identity and Access Management) solutions. We will adapt the plan based on available information and specific requirements identified during the project planning in Step 1.
We recommend that key personnel from the IT department (including service desk/support), HR/Payroll, and Digitalization/Service Development be part of the delivery group.
Meeting Frequency: We recommend weekly meetings during the phase 1 delivery period. Once the system is in normal operation, we recommend regular meetings between vendor and customer in order to make sure that the .
Cadence: Typically, meetings are more frequent initially (monthly or quarterly), eventually decreasing to 1-2 times per year. The frequency is decided by the customer.
Phase 1: Basic Setup - Defined automation
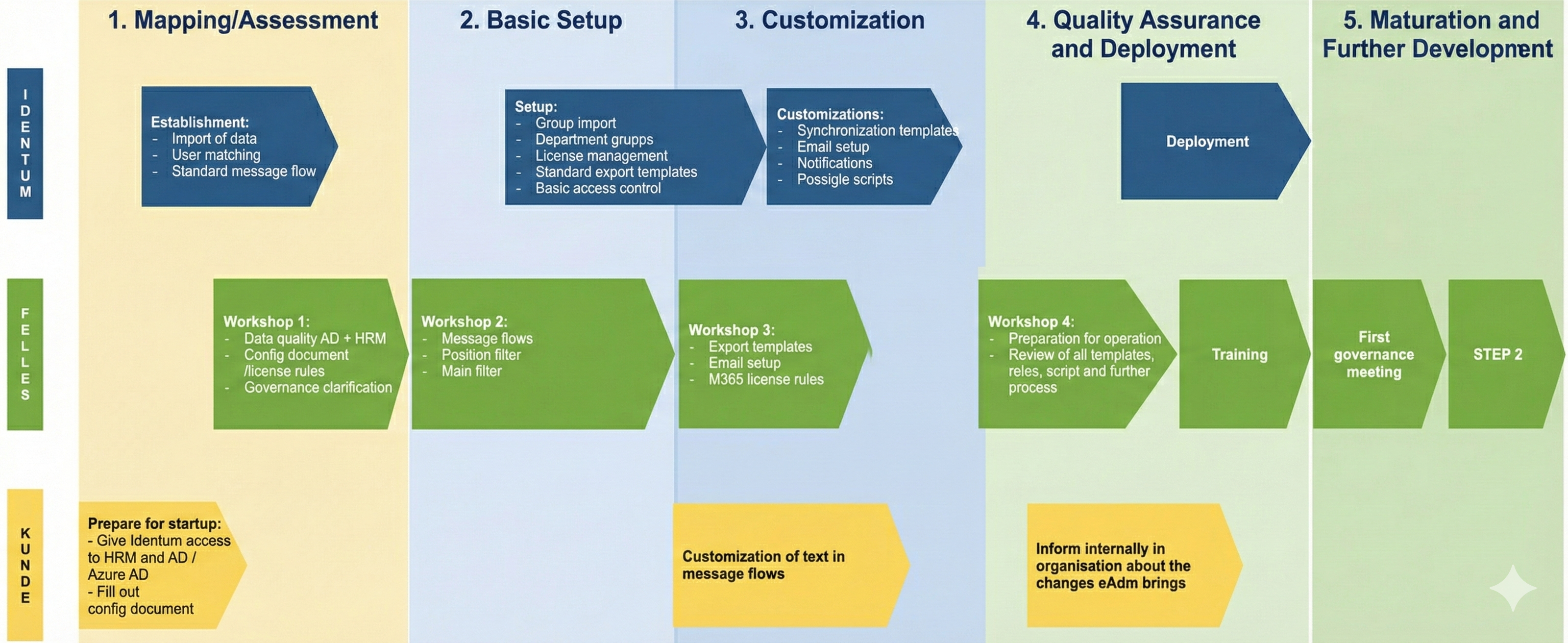
This phase consists of 5 steps where we revise and implement the blueprints attached to the contract.
Each step includes workshops where we further develop the setup together.
We recommend weekly status meetings to update each other on progress.
We use Trello for project management but can adapt to the customer's preferred tool if desired.
Mapping
In this phase, systems are set up, and data is imported from source systems.
Workshop: Assessment of data quality and discussion of potential corrective measures.
Prerequisites: The customer must grant necessary access before this phase begins. (Refer to technical documentation for access requirements).
Basic Configuration
Here, the fundamental workflows in the IAM solution are established.
Activities: Existing groups are imported from AD/Entra ID and integrated into access management systems. Synchronization templates for user data flow and a standard set of message workflows are set up.
Workshop Focus: Filtering of data (e.g., position/department filters) and a review of desired message workflows.
Customer Adaptation
This phase focuses on tailoring the basic setup.
Workshop Focus: Adapting data flows according to the customer's specific wishes and needs, setting up rules for email accounts, and M365 licensing.
Customer Action: Review chosen message workflows from the previous phase and adapt the text content.
Quality Assurance and Go-Live
This phase begins with a workshop to review the setup, plan for production, and set a date.
Deployment: When the delivery group agrees and the setup is approved, the vendor will deploy the system on the agreed date.
Internal Communication: The customer must conduct necessary information work internally, including informing management about the changes.
Training: Training in the use of the solution begins in this phase. The scope depends on the level of self-service implemented. For end-users, courses are typically offered via e-learning platforms.
Maturation and Further Development
This phase is a sliding transition to Step 2. During the 30-day run-in period, we review checklists to verify system functionality.
Feedback: It is crucial to gather feedback from management, HR, IT, and employees.
Adjustments: Adapt message workflows and access control rules based on feedback and fine-tune the setup.
Phase 1 Delivery Timeplan
A detailed GANTT schedule is typically created before we begin delivery, based on the agreed blueprints for phase 1.
Red: Work to be performed by the customer (e.g., HR or IT dept).
Blue: Work to be performed by the vendor.
Green: Work performed by vendor and customer together.
Yellow: Work performed by the customer.
Phase 1 Delivery Duration
This is very dependent on available customer resources! Typically 4 weeks for setup + 4 weeks run-in and fine-tuning period. The system is rolled out in stages rather than all at once. Production launch is when user account flow to AD/Entra ID is ready, then comes basic access control and message workflows. Connections to other target systems begin parallel to the run-in period. This means that if customer resources are limited, we can run the delivery in serial component delivery mode instead of (more or less) parallel.
Roles and Responsibilities
Identum or Identum partner (vendor): We can provide a project manager/coordinator with overall responsibility for progress, if desired.
Project roles are divided into Customer HR, Customer IT, Vendor, and Coordinator.
Customer Coordinator: We recommend that the customer appoint a coordinator for following up the delivery internally. This person is responsible for approving milestones required to proceed to the next step. It is recommended that the coordinator reports to the IT Manager or Executive Management if they are not part of the delivery group.
Estimated Resource Usage
We always include an estimate for our resource usage in the project scope, covering technical delivery of the setup as defined by the blueprints and the delivery schedule. Estimates may change if requirements or scope change during delivery.
Customer Recommendations:
Allocate enough resources for all project participants to attend weekly status meetings.
2-3 people should participate in each workshop.
Workshops are estimated to last half a day each.
Additional time is needed for training, internal information work, and adapting message workflows.
Phase 2: Advanced automation and beyond
The next phases builds upon the groundwork we laid in Phase 1, with activities depending on needs mapped out during the initial phase.
.webp?inst-v=bc8441ca-122a-4c2f-a38a-d25cdc32abc8)
Examples include:
Automatic downgrading or reclaiming of unused licenses.
Rules for deactivating employees on leave.
Cleanup of "Zombie accounts" in AD/Entra ID.
Need-based access control (access to specialized systems/secure zones only for employees with concrete needs).
Handling of user accounts for external users, contractors, and temporary staff.
Adding more connectors and integrations
Digital workflows for onboarding, external staff, access applications, etc
Execution: Tasks in Step 2 are proposed to be carried out by resource persons for the specific item in collaboration with the vendor, reporting back to the delivery group.
Training and Documentation Plan
We deliver a comprehensive training and documentation package to ensure the customer becomes self-sufficient in daily operations and future management of the Identum eADM platform.
Training Plan
Training is adapted to different user groups.
End Users (Employees, Managers): Digital training is offered via e-learning platforms and video resources (e.g., YouTube) covering common scenarios.
Service Desk Staff: Practical courses (approx. 2-4 hours) covering basic functions, troubleshooting, and user administration. It is advantageous for administrators to take this course before advanced training.
System Administrators:
Practical Involvement: Administrators participate in configuration, weekly meetings, and technical workshops ("learning-by-doing").
Formal Course: A dedicated 1-day administrator course focusing on advanced functionality, troubleshooting, and rule management.
Run-in Period: Close collaboration with consultants during the launch period provides further practical training.
Documentation
Documentation is tripartite to ensure relevance and currency.
General System Documentation: Publicly available and updated technical docs, user guides, and API references.
Customer-Specific Documentation: Delivered after the run-in period.
Blueprints: Visual description of architecture, data sources, rules, and flows.
Delivery Reports: Logs from project tools and workshop minutes.
Built-in Documentation: Descriptions embedded directly in the solution fields for rule sets, message flows, and templates. This ensures technical documentation remains precise and up-to-date.
Risk Matrix
Proper planning and preparation can mitigate risks. Key strategies include creating ownership in affected departments, thorough system mapping, and clearly defined goals.
Risk Factor | Measures | Responsibility | Risk Level |
Lack of ownership/participation from HR/Payroll | Involve HR/Payroll in regular meetings from the start; assign responsibility for data structure. | Customer | 3 |
Lack of ownership/participation from IT | Involve IT in technology selection; arrange workshops to increase ownership. | Customer | 2 |
Incomplete mapping of IAM needs | Perform GAP analysis of current vs. future needs; update requirements continually. | Customer/Vendor | 4 |
Lack of project scoping | Use Pareto principle for prioritization; regular project reviews. | Customer/Vendor | 3 |
Lack of internal resources | Create a resource plan early; assign temporary resources if needed. | Customer/Vendor | 4 |
Poor communication with end users | Establish communication strategy with updates; implement feedback systems. | Customer/Vendor | 4 |
Integrations with existing systems | Map all systems and integration requirements; test in staging environments before live. | Customer/Vendor | 4 |
Data security and privacy | Perform risk analysis and security tests; implement strict access controls. | Customer/IT Security | 5 |
User resistance to change | Communicate benefits early and often; involve users in testing. | Customer/Comms | 3 |
Time and budget overruns | Detailed project plan with milestones; regular reviews to adjust timelines. | Customer/Coordinator | 4 |
